Top 12 deep dives to understand the cybersecurity market
Deep Dives
Explore related topics with these Wikipedia articles, rewritten for enjoyable reading:
-
The Market for Lemons
11 min read
The article directly references and contrasts cybersecurity against the 'market for lemons' concept from George Akerlof's Nobel Prize-winning paper on information asymmetry. Understanding this foundational economic theory helps readers grasp why the author argues cybersecurity operates differently.
-
PayPal Mafia
13 min read
The article discusses 'mafias' from Splunk, Okta, CrowdStrike, and other security companies - alumni networks that spawn new startups. The PayPal Mafia is the original template for this phenomenon in tech, providing essential context for understanding how industry-shaping networks form.
There are now nearly 250 deep dives into Venture in Security, many of which are essential for understanding the market, whether you are a CISO, a security professional, founder, investor, or anyone else interested in building a well-rounded view of security. You know as well as I do that there are plenty of reports about individual market segments, but the fundamentals are critical regardless which segment you look at. Venture in Security covers the fundamentals. In this issue, I’ve compiled a selection of 12 of the most critical deep dives for anyone looking to truly understand our industry.
This issue is brought to you by… Tines.
Manual evidence collection, scattered tools, and repetitive audits can take a real toll on security and GRC teams. This new GRC playbook, created by Drata and Tines, offers a practical look at how teams are shifting to continuous, automated compliance.
Inside, you’ll find:
Detailed workflows for evidence collection, monitoring, audit prep, and vendor risk
Implementation guidance from credential setup to scaling
Best practices for building resilient, proactive GRC programs
Top 12 deep dives to understand the cybersecurity market
Why there are so many cybersecurity vendors, what it leads to and where do we go from here
It is common to hear that there are “too many vendors” in cybersecurity, and that “we don’t need 200+ products in the same category doing the same thing”. What is rare is seeing analysis as to why there are so many similar vendors - what is driving the establishment of the new companies, and fueling the cybersecurity gold rush.
In this article, I am looking at some of the factors that lead to the emergence of hundreds of “me too” startups, why relatively few businesses in the industry fail and equally, few win big, and why there are only 18 pure-play cybersecurity companies listed on the US stock exchange.
It’s been nearly 3 years since I published this article but it is as relevant today as it was back then.
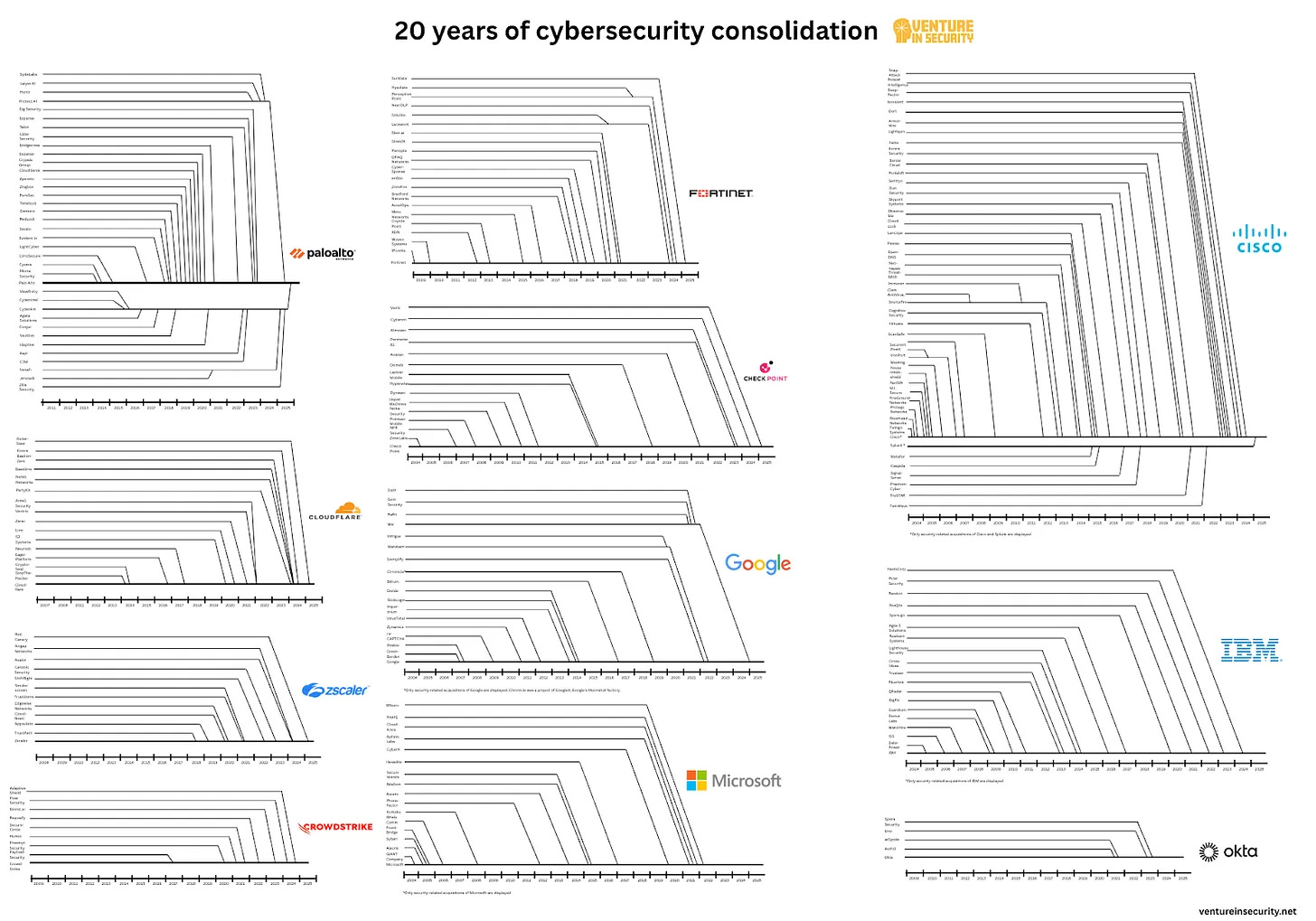
20 years of cybersecurity consolidation: how 200 companies became 11
Everyone in cyber likes to talk about consolidation but very few people understand how it looks in the wild. This isn’t a usual article, it’s a lookback at the past 20 years of consolidation history in our industry. Here’s a preview:
12 ways to fail a cybersecurity startup
“Why do startups fail?” is one of the
...This excerpt is provided for preview purposes. Full article content is available on the original publication.