Understanding SkyWater
Deep Dives
Explore related topics with these Wikipedia articles, rewritten for enjoyable reading:
-
Power Macintosh
14 min read
Linked in the article (18 min read)
-
Cell (processor)
15 min read
Linked in the article (29 min read)
-
Mubadala Investment Company
11 min read
Linked in the article (6 min read)
If you like any of the following:
American semiconductor manufacturing
US national security
Rock’s Law
Berkshire Hathaway-style acquisitions
Quantum computing
Then you’re going to enjoy the story of SkyWater Technology, a pure-play semiconductor foundry in America’s heartland.
This will be a long and fun walk through the history and strategic choices that shaped the company, from why it exists at all to the specific playbook it’s using to grow.
First, to understand how SkyWater emerged, we need to rewind and look at the semiconductor industry's history that made its founding possible—nay, necessary. Then we can examine its differentiated strategy and future upside.
We start with the intersection of national defense and semiconductors.
Chapter 1: National Security and the Trusted Foundry Program
For decades, the United States has relied on the simple idea of deterrence through technological asymmetry; stay ahead by fielding technologies no rival can match.
Semiconductors have been the backbone of that strategy. They powered the guidance computers in Minuteman missiles in the 1960s, the radar and signal processors that made stealth aircraft viable in the 1980s, and the high-speed digital logic that enabled GPS-guided weapons in the 1990s.
In the early years, defense electronics were built by American integrated device manufacturers that designed and fabricated their own chips—think Fairchild and Texas Instruments.
Over time, however, manufacturing migrated overseas. First in assembly and test, then memory and logic, as pure-play foundries such as TSMC (1987) and UMC (1995) enabled the rise of fabless companies.
Rock’s law accelerated this shift:
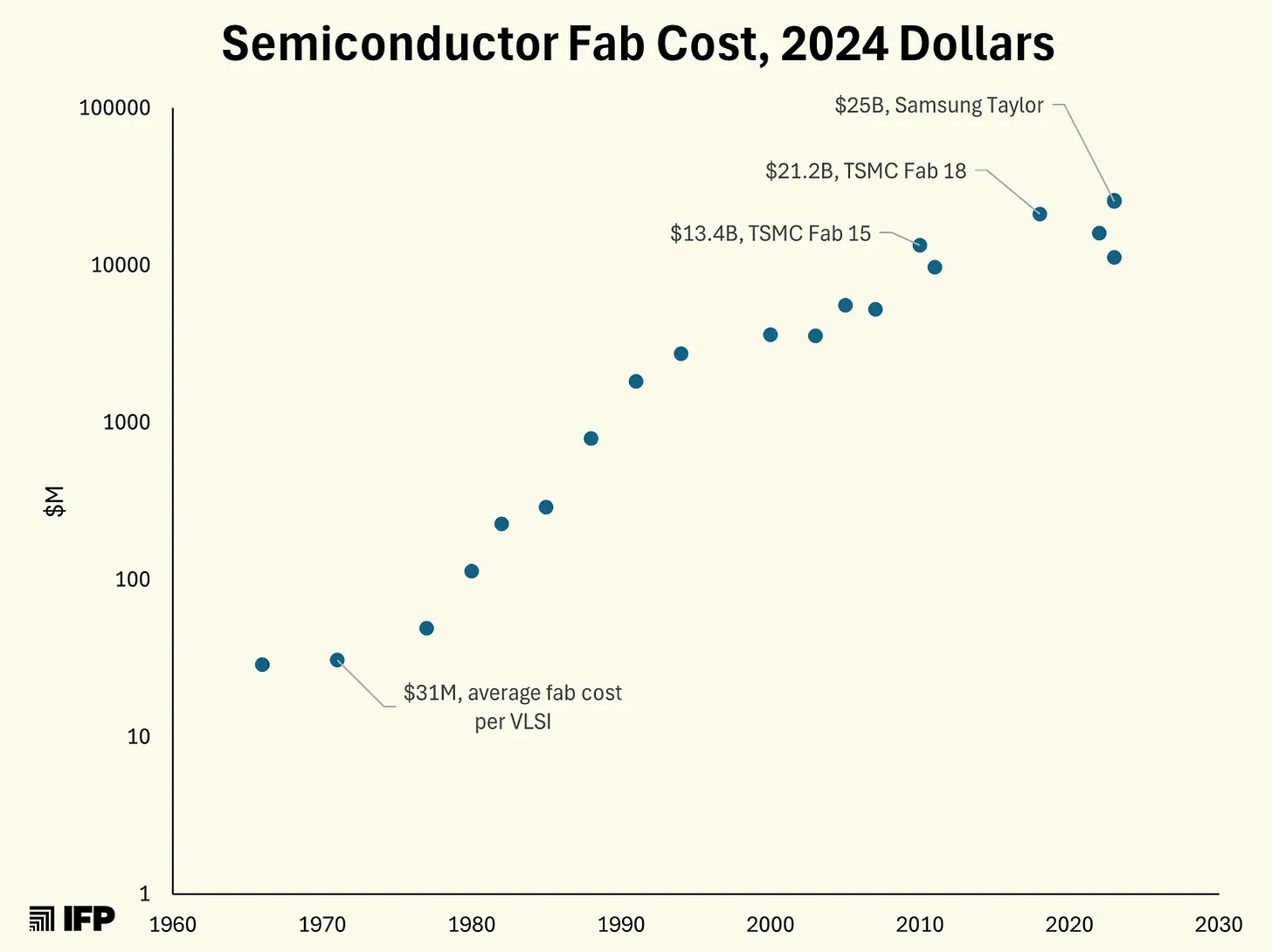
Don’t forget that chart, as it’s central to this story and much of semiconductor history.
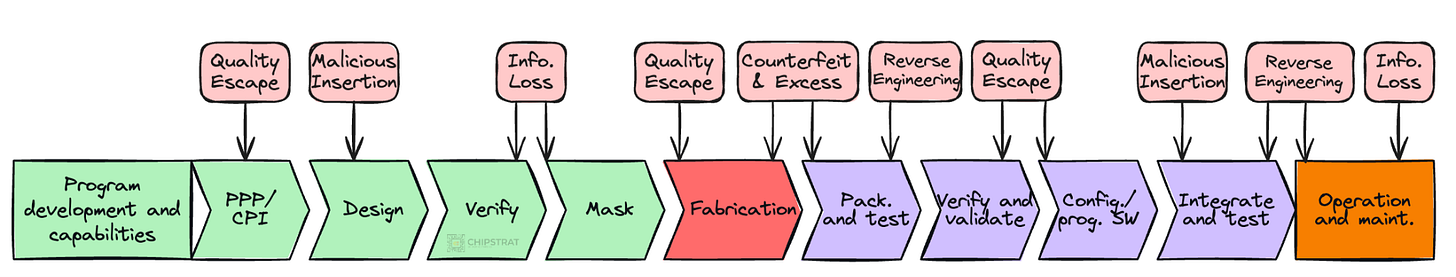
As economics and specialization pushed more of the supply chain overseas, it created openings for adversaries to tamper with hardware, extract IP, insert backdoors, and introduce counterfeits. Here’s an example of what can happen at various steps in the chip lifecycle:
The Pentagon recognized the need for secure, on-shore production of the entire end-to-end supply chain.
That concern led to the Department of Defense and NSA launching the Trusted Foundry Program. Its goal was simple: ensure that the nation’s most sensitive chips could still be built, tested, and verified within U.S. borders.
The Trusted Foundry Program began as a long-term sole-source arrangement with IBM Microelectronics, which operated trusted fabs in Vermont and New York.
...This excerpt is provided for preview purposes. Full article content is available on the original publication.